
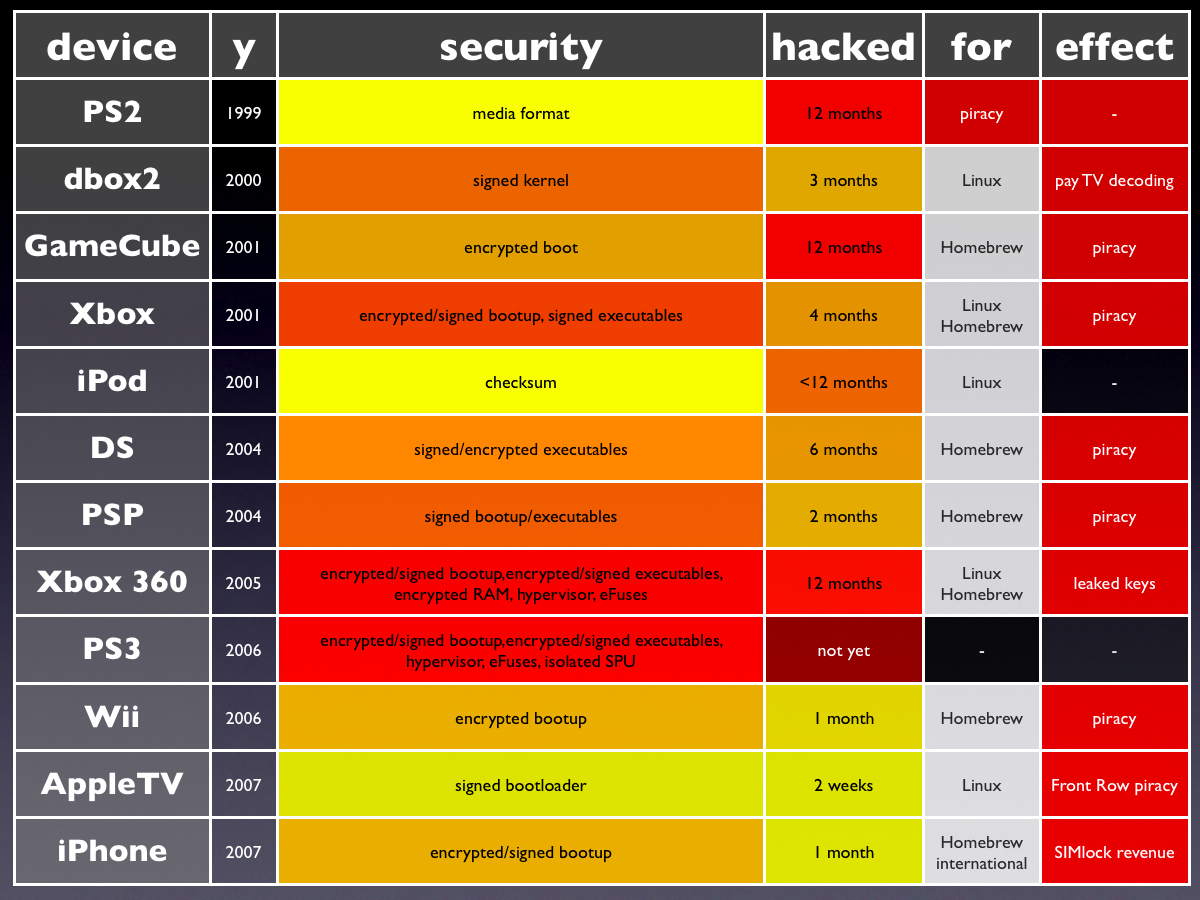
The table shows the relationship between the quality of a device’s security system and the time it took to hack it, as well as the original motivation for hacking and the side effects (collateral damage) it caused.
Correlation security/time to hack
There is a pretty clear correlation betwen the quality of the security system and the time required for hacking it – with the notable exception being the GameCube, which had rather weak security, but since its release coincided with the much more powerful Xbox, much of the hacker community neglected the GameCube until the Xbox was done. What can also be seen is that recently, devices tend to get hacked more quickly; probably simply because there are more and more people interested in hacking.
Correlation Linux/time to hack
The other exception is the PlayStation 3, which was not hacked until about three and a half years after its introduction. I argued that this was because there was only very little motivation to hack it: Sony shipped the devices with the “Other OS” option and even sponsored a port of Linux to it, allowing any user to install Linux if they wanted. Although Linux was running on top of a hypervisor and did not have access to all of the features of the device, it seems to have been enough to take the enough motivation to hack it out of the hacker community.
Linux/homebrew is the primary motivation
(Here is an updated 2010 version of the table:)
device | y | security | hacked | for | effect |
PS2 | 1999 | ? | ? | piracy | - |
dbox2 | 2000 | signed kernel | 3 months | Linux | pay TV decoding |
GameCube | 2001 | encrypted boot | 12 months | Homebrew | piracy |
Xbox | 2001 | encrypted/signed bootup, signed executables | 4 months | Linux Homebrew | piracy |
iPod | 2001 | checksum | <12 months | Linux | - |
DS | 2004 | signed/encrypted executables | 6 months | Homebrew | piracy |
PSP | 2004 | signed bootup/executables | 2 months | Homebrew | piracy |
Xbox 360 | 2005 | encrypted/signed bootup,encrypted/signed executables, encrypted RAM, hypervisor, eFuses | 12 months | Linux Homebrew | leaked keys |
PS3 | 2006 | encrypted/signed bootup,encrypted/signed executables, hypervisor, eFuses, isolated SPU | 4 years | Piracy Homebrew | - |
Wii | 2006 | encrypted bootup | 1 month | Linux | piracy |
AppleTV | 2007 | signed bootloader | 2 weeks | Linux | Front Row piracy |
iPhone | 2007 | signed/encrypted bootup/executables | 11 days | Homebrew SIM-Lock | piracy |
iPad | 2010 | signed/encrypted bootup/executables | 1 day | Homebrew | piracy |
AS YOU CAN SEE THE PS3 SECURITY ISSUE WAS WELL KNOWN FOR A LONG TIME
SONY DID NOTHING TO MAKE UP TO ITS END USERS FOR THE REMOVAL OF OTHER OS AND THE MAJOR DOMINO EFFECT IS BEING FELT BY ALL 77 MILLION PSN USERS
SO CALL 1-800-345-SONY AND ASK IF SONY HAS A REASON TO SHIT ALL OVER ITS END USERS THEN ASK QUESTIONS LIKE "WHY ARE THESE HACKERS SO MAD AT US" see if they admit the removal of other os caused the hacking of the ps3 by TEAM FAIL OVERFLOW a VERY long while ago! ...FACT IS SONY HAS FAILED US ONCE AGAIN...
This is supported by the by the fact that the motivation for hacking every system in the table was either homebrew (i.e. running unautorized hobbyist applications) or Linux. Hackers seem to love to convert their devices into Linux computers to run a big library of existing software, or to hack the device to make it possible to run versions of existing emulators and games on the native OS.
Piracy is a side effect
None of the hacks in the table was done with the motivation to allow running copied games – but whenever the point of the security system was to prevent piracy, hacking it inevitably enabled piracy as a side effect. Some security systems protected other things like pay TV keys and SIM-locks; these also fell as side effects.
2010 update
In September 2009, Sony started shipping the “slim” model of the PlayStation 3, with the “Other OS” feature removed. With firmware 3.21 in April 2010, the feature was also removed from existing original models that users chose to upgrade – which was required for using any of the online features. The missing “Other OS” feature on the slim model motivated George Hotz (geohot) to hack into hypervisor mode (Jan 2010), but this approach did not lead to a working hack of the security system. In August 2010, the Australian company OzMods announced the commercial “PSJailbreak” USB dongle that hacks into non-hypervisor mode, allowing piracy and homebrew (“Backup Manager” says “backups and homebrew”).
Although this is the first time that a commercial company is first to hack a system, and the first time that piracy seems to have been a key motivation, removal of “Other OS” might have been another motivation, and geohot’s previous attempts might have helped as an entry point for this hack.
Usually, an open hacker community develops a hack, and commercial companies convert them into modchips. This time, a company developed a hack and a modchip, and the community reverse engineered it and ported the exploit code onto several other devices, allowing people to hack the PlayStation 3 without a dedicated device. And I’m sure Linux will be adapted soon to run in the new environment.
Conclusion
What do we learn from this? Linux is inevitable. Or maybe it should be “Homebrew is inevitable”. In the history of mankind, there has yet to be a popular system that is locked down to only allow certain software to run, but does not get hacked to run arbitrary code. I still dare to say that if Sony had not removed “Other OS”, the PlayStation 3 would have been the first system to not get hacked. At all.
No comments:
Post a Comment